Posts

My current skillset
One of my goals is to be skilled in all IT service management areas to become an all-encompassing IT Leader. To track my progress, I created this chart indicating my experience with various IT service management practices as outlined by ITIL v4.
Since my last update in October 2020, I increased my skillset significantly in the following areas:
Measurement & Reporting Supplier Management Workforce and Talent Management The blue areas where I have the least amount of experience are the ones I’m currently concentrating on.

New work and SaaS
The challenge Transparency is one of the key elements creating self-managed teams and enabling people to make informed decisions in progressive organisations.
Every single activity we conduct at work — recruiting, sales, accounting — is dependent on information processing and knowledge transfer. If we can tap into our collective intelligence, we can accomplish amazing things. And so it’s somewhat surprising how little time we spend on our information architecture — our approach to discovering, storing, and sharing what we know.

My current skillset
One of my goals is to be skilled in all IT service management areas to become an all-encompassing IT Leader. To track my progress, I created this chart indicating my experience with various IT service management practices as outlined by ITIL v4.
The blue areas where I have the least amount of experience are the ones I’m currently concentrating on.

To cloud or not to cloud
The question of how to integrate cloud service providers as part of the IT strategy is one of the tougher questions IT leaders are currently facing. In this blog post, I’ll outline our thought process and the conclusion derived.
For the sake of this blog post, we’ll peruse the definition of “cloud computing” by NIST:
“Cloud computing is a model for enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources (e.
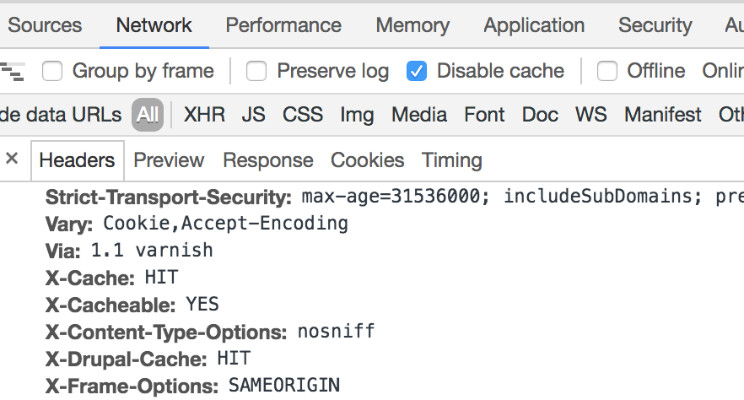
HSTS - How to implement HTTP Strict Transport Security (HSTS)
Please find my latest blog post how to implement HSTS here: https://wiedemeier.space/blog/hsts/
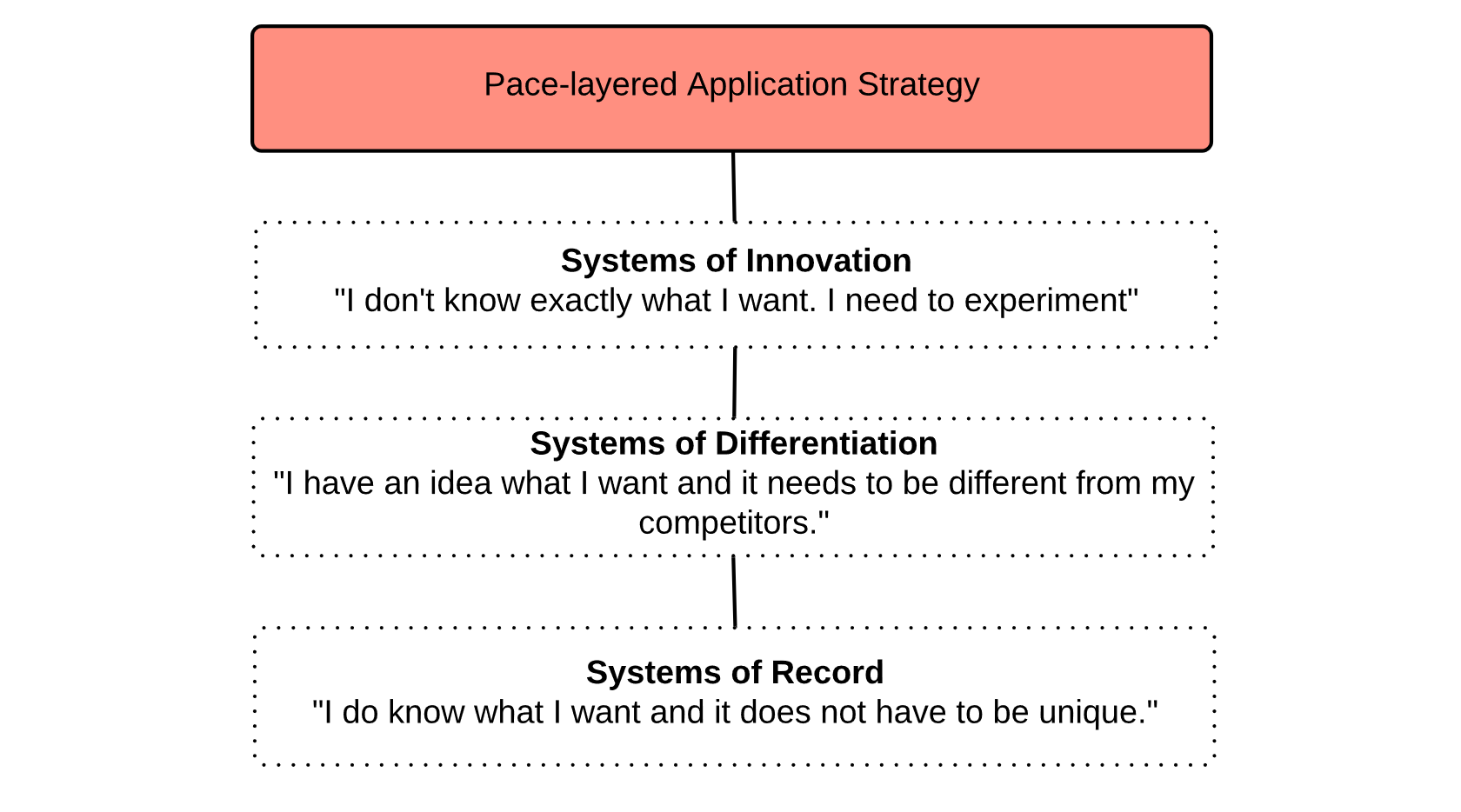
Strategy
Edit 2023-01-08 - this blog post was initially published on https://www.unic.com/en/competencies/experts-blog/2017/effective-it-strategy but deleted - I copied here for future reference:
One of the key challenges in IT is that not every system is created equal. When developing services we try to harmonize the way we manage IT systems and the applications provided by them. However, we see an increasing tension between flexibility and reliability. Very generally we want agility when it comes to systems that allow us to work and collaborate in new ways.
TLS - Time to finally implement TLS everywhere
This blog was previously posted here: https://www.unic.com/en/competencies/experts-blog/2017/website-available-through-tls but has since been deleted.
Google Chrome – with a market share of 60% the currently most used web browser [^1] – will mark user entry on HTTP-pages as “Not Secure” from version 62 onwards (due October 2017). [^2]
It is a stated goal of the Chromium project (the open source community developing the Chrome browser) to mark all HTTP pages as “Not secure” in Chrome [^3]: