Using hugo static site generator and netlify continuous integration (from github), I created a small static website for a local business. I also wanted to make sure, the site is secure and get’s the highest score on Mozilla observatory:
| Score | Rule | Description |
|---|---|---|
| 0 | x-xss-protection | X-XSS-Protection header set to “1; mode=block”. |
| 0 | cookies | No cookies detected. |
| 0 | cross-origin-resource-sharing | Content is not visible via cross-origin resource sharing (CORS) files or headers. |
| 0 | public-key-pinning | HTTP Public Key Pinning (HPKP) header not implemented. |
| 0 | redirection | Initial redirection is to https on same host, final destination is https. |
| 0 | contribute | Contribute.json isn’t required on websites that don’t belong to Mozilla. |
| 0 | strict-transport-security | HTTP Strict Transport Security (HSTS) header set to a minimum of six months (15768000). |
| 0 | subresource-integrity | Subresource Integrity (SRI) not implemented, but all scripts are loaded from a similar origin. |
| 0 | x-content-type-options | X-Content-Type-Options header set to “nosniff”. |
| 5 | referrer-policy | Referrer-Policy header set to “no-referrer”, “same-origin”, “strict-origin” or “strict-origin-when-cross-origin”. |
| 5 | x-frame-options | X-Frame-Options (XFO) implemented via the CSP frame-ancestors directive. |
| 10 | content-security-policy | Content Security Policy (CSP) implemented with default-src ‘none’ and no ‘unsafe’. |
The final score is a personal record of: 120 - Grade: A+
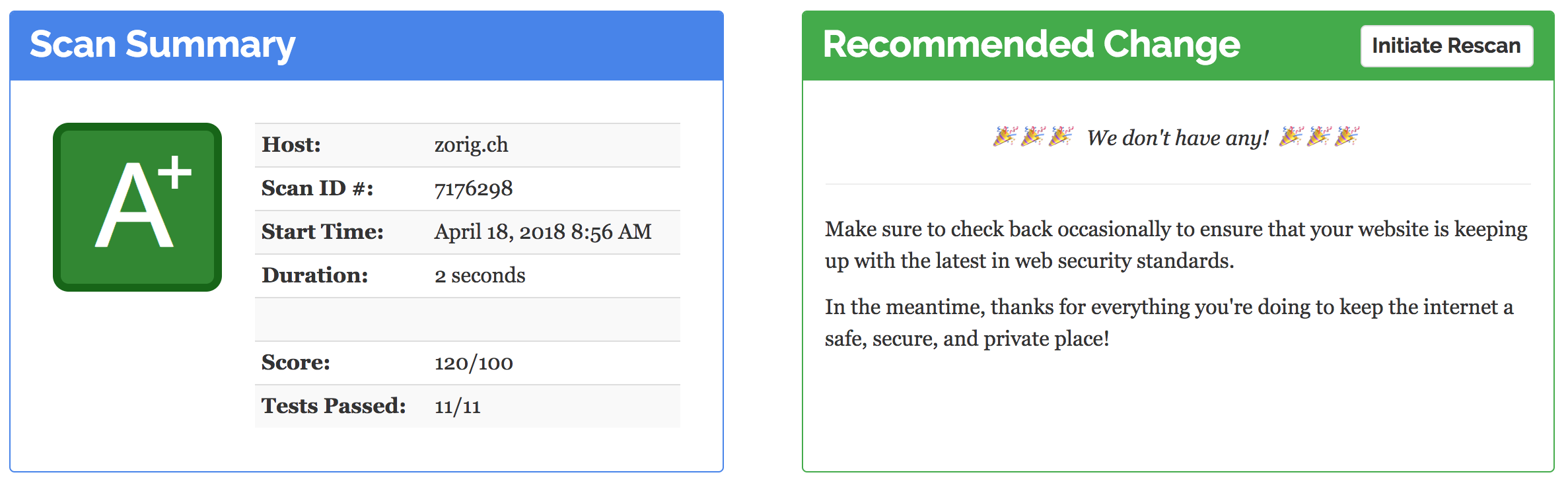
Full Report Url: https://observatory.mozilla.org/analyze.html?host=zorig.ch